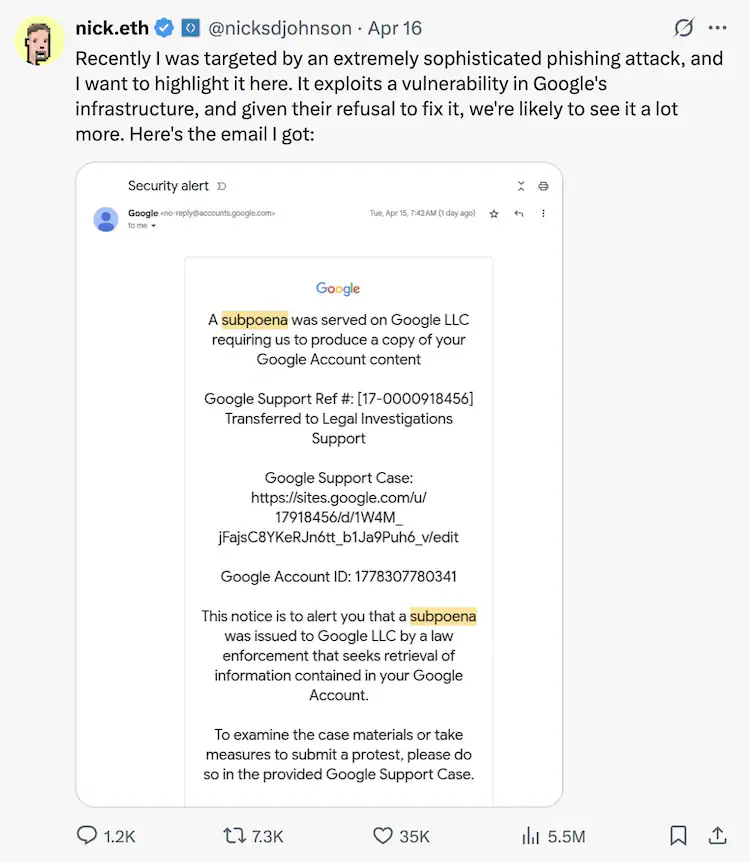
A sophisticated phishing campaign is targeting Gmail users by sending emails that appear to originate from Google’s official address, “no-reply@google.com.” These emails claim that the recipient’s account is under legal scrutiny, urging them to click on a link to review purported subpoena details.
The scam exploits Google’s own infrastructure by using the Google Sites platform to host counterfeit support pages. These pages closely mimic legitimate Google interfaces, making it challenging for users to discern the fraud. The attackers have managed to bypass standard email authentication protocols, such as DomainKeys Identified Mail (DKIM), allowing these phishing emails to pass through spam filters and appear in the same conversation threads as genuine Google alerts.
Nick Johnson, a developer with the Ethereum Name Service, was among those targeted. He reported the incident to Google, highlighting the misuse of Google’s OAuth applications. Initially, Google dismissed the concern, stating it was “working as intended.” However, the company has since acknowledged the vulnerability and is working on a fix.
In response to this threat, Google advises users to enable two-factor authentication (2FA) and consider adopting passkeys for enhanced security. Passkeys are cryptographic credentials that provide a more secure alternative to traditional passwords and are resistant to phishing attacks.
Users are urged to exercise caution with unsolicited emails, especially those requesting personal information or prompting immediate action. It’s recommended to verify the authenticity of such messages by accessing account settings directly through Google’s official website, rather than clicking on links within the email.
To report suspicious emails, Gmail users can use the “Report phishing” option found in the three-dot menu of the message. This helps Google identify and mitigate similar threats in the future.

